Annualized data from blockchain forensics provider Chainalysis indicates that crypto-enabled crime has dropped precipitously through the first half of 2023, but cybercriminals are also continuously evolving new cash-out methods to cover their tracks.
Chainalysis’s mid-year update found that crypto inflows to “known illicit entities” were down 65% compared to where they were last June. Meanwhile, crypto flows to high-risk entities, which generally entail “mixers” and non-compliant exchanges were down 42%. Crypto mixers are protocols that enable large groups of users to pool their funds together in a deposit wallet that is programmed to redistribute tumbled crypto assets back to designated receivers.
Specifically, mixer protocols scramble large clusters of crypto deposit inputs and transfer outputs together, making it difficult for blockchain sleuths to determine what the initial sources of a mixer recipient’s funding streams are. Mixers can thus help threat actors obfuscate the illicit origins of their crypto, although blockchain forensics tools can still detect mixer service wallet addresses and any outputs that receive funds from them. Still, mixed crypto fund flows only indicate heightened risk, not smoking-gun evidence of criminality.
Recent examples of infamous and now-dismantled mixing services include Helix and Tornado Cash. But an endless array of new mixer services continue to proliferate on cybercriminal forums. Meanwhile, the scam category is the most significant driver of diminishing, illicit-crypto fund flows. Scam losses were roughly $3.3 billion less through mid-2023 than they registered through the previous June, according to Chainalysis. Scams typically entail pump-and-dump or rug-pull frauds that hype up decentralized finance (DeFi) assets or non-fungible tokens (NFTs).
Investment scams are also increasingly manifesting as so-called “pig butchering” frauds.
In these scams, predominantly Asia-based threat actors lure unsuspecting victims via text message outreach or on social media and convince them to invest large sums in high-yield investment vehicles. While crypto crime appears to be declining significantly, it should be noted that this outlook is based on wallet addresses that Chainalysis was able to identify as illicit. The depths of Chainalysis’ blind spots remain unknown, and criminals are continuously innovating.
Moreover, the latest data from crypto security firm De.Fi warned that it was increasingly becoming harder to recover illicit-origin crypto assets, despite the steep decline in digital asset transactions linked to crime. It follows that financial crime professionals and investigators must entertain the unsettling thought that threat actors may also be getting better at concealing the illicit nature of their funding streams.
To wit, Cryptosec combed the dark web and discovered what has been touted by some in the cybercriminal underground as the “most complete manual for withdrawing a crypt[o] that does not pass AML verification.” The following blog will examine this manual and spotlight some of the most emergent tactics for the stealth cash-out of illicit-origin crypto assets.
Rags to Riches’ Guide to Cashing Out Dirty Crypto
Cryptosec uncovered the aforementioned crypto-cash-out manual in a Russian-language Telegram channel posting from January 31. This TG channel is both a dark-web link aggregator and an informational resource for hackers and privacy conscious Internet users. The channel attributed this post to a user or channel operating under the handle, ‘rags to riches’.

This manual breaks down the withdrawal process into two categories: ‘Reception/Storage’ and ‘Cleaning/Output’. In the reception/storage section, the author notes: “First, we need to get out Bitcoins somewhere, which will not pass verification.” When the author says verification, they are referring to anti-money-laundering (AML) screening.
In crypto, virtual asset services providers (VASPs) must screen funds deposited into their wallet addresses for indicators of illegal activity. Examples of activity flagged by compliant VASP’s AML programs are funds linked to ransomware, dark-net-market (DNM) commerce, scams, mixers, gambling websites, and other high-risk categories.
Due to maturing AML oversight models globally, the guide notes that crypto launderers “can’t go directly to an exchange or an exchanger,” as funds “can be frozen.” Instead, the guide advises would-be threat actors to use a staging wallet that requires no AML checks. They also advise readers to use a wallet that generates a unique, one-time address each time it receives funds. “All these functions are perfectly performed by the Electrum cold wallet,” advises the manual.
First launched in 2011, Electrum is one of the oldest crypto wallets in operation. This wallet only supports Bitcoin. Electrum is also compatible with hardware wallets like Trezor and Ledger. As a cold-storage crypto repository, Electrum enables crypto users to keep their private keys offline, and “go online with a watching-only wallet,” according to organizational marketing literature.
This crypto wallet also comes standard on The Amnesic Incognito Live System (TAILS), a portable, thumb-drive-loaded operating system “that protects against surveillance and censorship,” per TAILS marketing copy.
Naturally, this portable operating system, which is programmed by default to forget all data from my previous user sessions, is highly popular with many dark web users. On cybercriminal forums, threat actors routinely advise others to use Tails in combination with TOR and a VPN connection, for example.
The rags to riches guide also touts the above setup, noting that Electrum wallets are “best used in a virtual machine or sandbox that redirects traffic through the Tor network, after enabling the VPN.” Once logged into TAILS and connected to the web via VPN, the guide says it’s safe to open the Electrum wallet. “Here we will accept the crypt and immediately store it and divide it into parts if necessary,” notes the guide.
Cleaning/Output
Once staged in the Electrum wallet, the guide notes that “we need to withdraw bitcoins into real currency,” and specifies several methods of doing so. The first method entails transferring funds from Electrum to the Onion Market exchanger. Onion Market is a free and TG-native, crypto exchanger. This TG application enables the exchange of Bitcoin, Monero, Litecoin, and TON (Telegram’s in-app cryptocurrency).
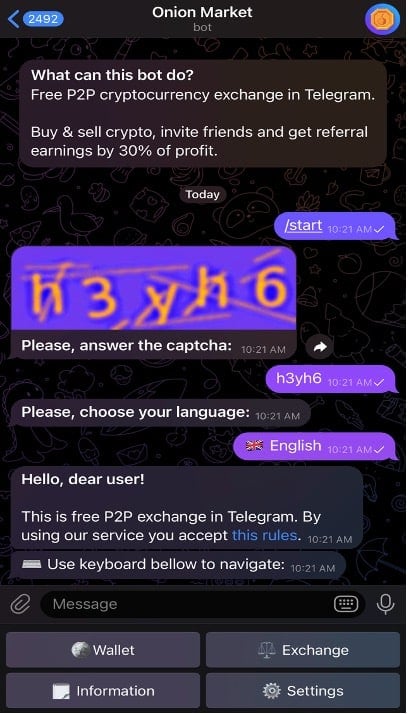
Like many exchangers, Onion market does not perform any AML or Know Your Customer (KYC) checks. Also, unlike institutional crypto exchanges like Coinbase or Binance, Onion Market is a peer-to-peer crypto exchanger. The platform is just an intermediary that enables no-KYC transactions between peers and conversions between cryptocurrencies. The guide notes that Onion Market users “can withdraw money to the card right from here.”
However, the manual cautions that while the exchanger will not block transactions tainted by criminal activity, it will record “the connection of the ‘dirty’ transaction with the card.” Therefore, the guide advises users to use a ‘drop’ card to withdraw funds from their Onion Market account.
Drop accounts are frequently operated by money mules, or underlings that take a small percentage of the funds that transit their accounts. But most importantly, drop cards should obviously never be issued in the name of the person withdrawing illicit funds. Alternatively, ‘hot’ crypto funds could be sent from Electrum through a “mixer before being entered into the exchanger,” says the manual.
The guide proposes a second cash-out scenario that eschews the exchanger function entirely. Instead, this cash-out relies on cryptocurrency conversion. Specifically, the guide proposes converting Bitcoins to Monero. Monero is an anonymity-enhancing cryptocurrency that leverages three different privacy technologies: ring signatures, ring confidential transactions (RingCT) and stealth addresses.
Ring signatures basically function as a built-in mixer. This means that when Monero funds are sent, senders arbitrarily select multiple other Monero users’ funds to also feature in the transaction log as possible senders. RingCT “hides not only the source of funds being sent, but also hides the amounts of the funds being sent from being visible on the blockchain,” according to the Monero website. Meanwhile, one-time stealth addresses are a self-explanatory feature.
However, the manual highlights Onion Market’s relatively low Monero exchange limit for users attempting to convert large amounts of Bitcoin. Regardless, “in order to unequivocally break our connection with the original money,” advises the manual, “we need to make at least one transaction in Monero.” The guide says that the “Bitpapa wallet is the best” for this chain-breaking transaction.

Bitpapa is a UAE-registered crytpo exchange that offers users “over 100 payment methods” to make their trades, according to the company’s website. In addition to Bitpapa’s “convenient acceptance in Monero and P2P-exchange of coins directly to the card, there is no mandatory verification, and only mail is needed for” user registration, notes the guide.
Takeaways
On Telegram, this post generated 17 likes, three clown emojis, one poop emoji, and 11 comments.

One of the Telegram users who commented on the post, noted that there were many similar crypto cash-out services being marketed on Rutor, which has emerged as the most popular darknet forum since the demise of Hydra. Another user, going by the handle, ‘Ivett DarkWave Witch’ advised that transitioning to cash-based payment rails increases risk and that drop cards should be used when transacting through Bitpapa.

Besides Electrum, other secrecy-friendly wallets recommended in Russian cybercriminal TG communities include Trust Wallet, MetaMask, and Blue Wallet.

While reports of decreasing crypto-crime, increased blockchain tracing capacity, and heightened regulatory oversight are encouraging, financial crime fighters must consider the evolving sophistication of the adversaries they are pursuing. The Cambrian explosion of the money-laundering-as-a-service (MLAS) economy on the dark web makes the pursuit of financial integrity in crypto markets that much more challenging.
At Cryptosec, we are trying to build a safer and more compliant crypto community. Keeping pace with the latest crypto-laundering threat intelligence is essential to secure the attack perimeter in a rapidly evolving AML risk landscape.






 Beware of crypto recovery scammers falsely claiming ties with us. Learn
Beware of crypto recovery scammers falsely claiming ties with us. Learn